MRMCD23: JWT Next Try
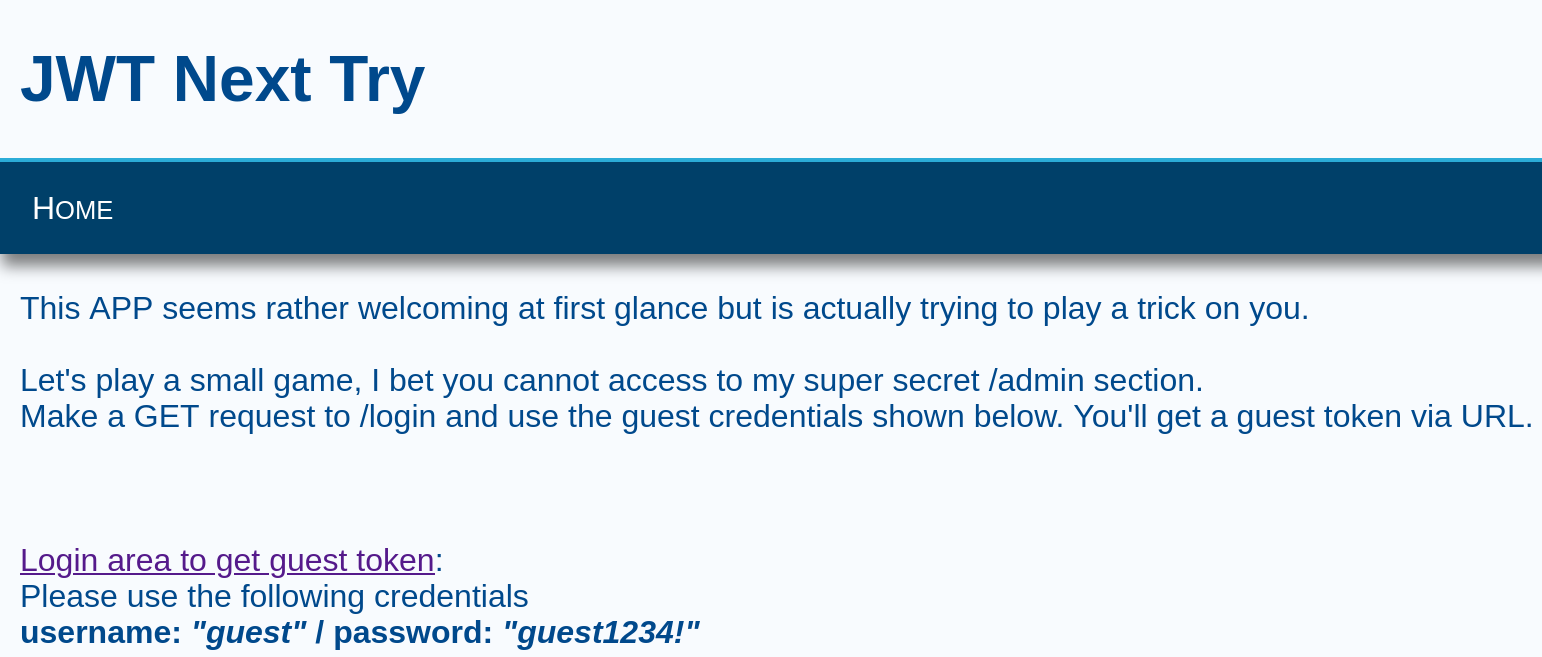
Task
Ok this time the implementation is absolutely flawless! My JWTs are stronger than your pathetic hacking attempts.
Solution
I logged in with the provided credentials, which generated a JWT. The site behind the login page also reveals a link to the admin panel (Login for Admins). Since the text stated, that the implementation is absolutely flawless, I thought about what could go wrong besides implementation. Clearly passwords/key strength! So I took the generated JWT and had a look at it with jwt.io. But first the JWT:
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJ1c2VyIjoiZ3Vlc3QiLCJleHAiOjE2OTk2NTc1OTd9.MSkvOTMzczDnpy_rnL5E9xFOxRxzND9Ot4wbcf2JTqsOUrAc3rGXnM-lwxGV3dyJL5r9vS1GjWI5MvOhLHYqsQ
A JWT consists of a header, a payload and a signature. In our case we had the following header:
{
"typ": "JWT",
"alg": "HS512"
}
The following payload:
{
"user": "guest",
"exp": 1699657597
}
And the following signature (obviously not decoded):
MSkvOTMzczDnpy_rnL5E9xFOxRxzND9Ot4wbcf2JTqsOUrAc3rGXnM-lwxGV3dyJL5r9vS1GjWI5MvOhLHYqsQ
Since I wanted to access the admin panel and thought about weak keys/passwords I wanted to generate a JWT for the user ‘admin’ to access the admin panel. So I tried brute forcing it, trying differend wordlists I found online. At the actual event I solved it with a script I found online, but it is easily possible with john:
john jwt.txt --wordlist=shortKrak.txt --format=HMAC-SHA512
The password was Mellon which was included in the shortKrak wordlist. Now it was very easy to create an admin JWT with the help of jwt.io, I just had to send a GET request with that JWT to the path /admin. The admin panel showed the follwing text:
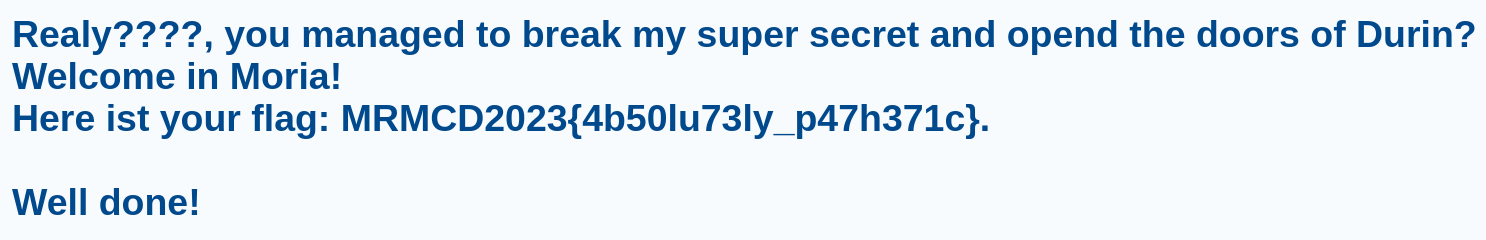
So, that’s it:
MRMCD2023{4b50lu73ly_p47h371c}
Solved by petrosyan